Executive summary – what changed and why it matters
AWS expanded Amazon Bedrock AgentCore at re:Invent with three practical additions: natural‑language Policy controls integrated with the AgentCore Gateway, AgentCore Evaluations (13 prebuilt checks for correctness, safety and tool use), and AgentCore Memory (user and session logging for personalization). These changes convert AgentCore from an orchestration runtime into a packaged, production‑ready agent platform that reduces engineering lift for governance, validation and personalization.
- Impact now: Immediate reduction in deployment risk through integrated policy enforcement and automated evaluations; faster time‑to‑production for regulated enterprise use cases.
- Quantified detail: Evaluations ship with 13 prebuilt checks; AgentCore and the expanded toolset are generally available across major AWS Regions (GA Nov 2025).
- Main tradeoff: Memory and evaluations improve quality and obedience but introduce new privacy, retention and audit requirements that teams must operationalize.
Breaking down the announcement
Substantive change: AgentCore now includes three integrated capabilities that target the three largest barriers to enterprise agent adoption: enforceable boundaries, automated correctness/safety checks, and contextual memory. Combined with the broader AWS agent portfolio (Nova Act for UI automation, Transform agents for modernization, Strands for orchestration, etc.), the platform is positioned to run end‑to‑end autonomous workflows in production.
Policy controls + AgentCore Gateway
AWS added natural‑language policy definitions that map to enforcement points in the AgentCore Gateway. In practical terms, you can write human‑readable constraints (“do not exfiltrate customer PII”, “never call production APIs without approval”) and the gateway will block actions that violate those rules. That reduces custom middleware and provides a single point to audit denied actions.

AgentCore Evaluations (13 prebuilt checks)
Evaluations supply 13 out‑of‑the‑box checks covering correctness (does the agent’s proposed action match intent?), safety (hallucination, policy adherence), and tool use (parameter validation, side‑effect checks). These checks can run pre‑commit or at runtime, giving engineering teams an automated gate that previously required bespoke testing frameworks.
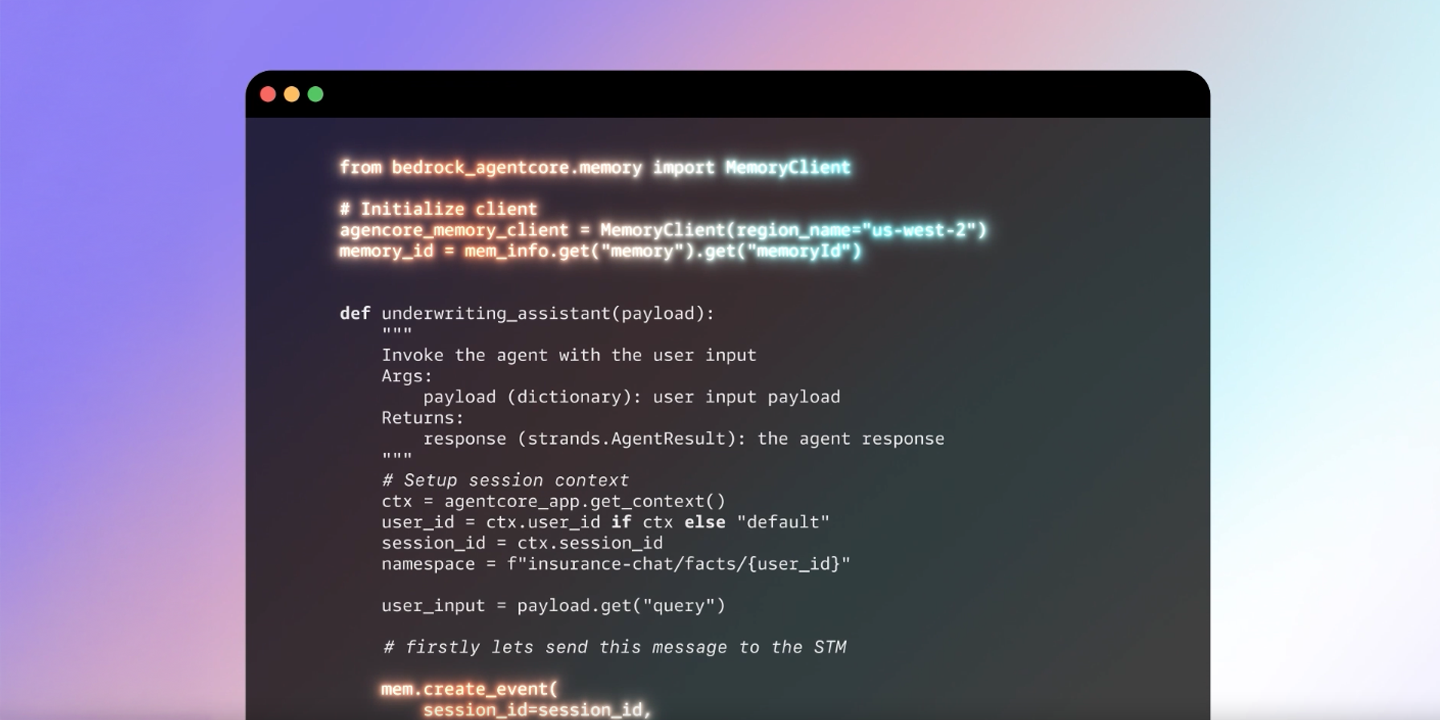
AgentCore Memory
Memory captures user interactions and session state for personalization, continuity, and context‑aware decisions. AWS positions this for improved agent performance across multi‑turn workflows, but it shifts responsibility for data lifecycle management, consent tracking, and eDiscovery onto operators.

Why this matters to operators and product leaders
Short answer: the platform reduces engineering and policy overhead needed to run agents in regulated contexts, which accelerates adoption for internal automation (IT ops, migration, support) and external facing agents (client portals, support bots). The prebuilt evaluations and gateway enforcement convert “pilot‑only” deployments into governable production services faster.
Risks and governance considerations
- Data privacy and compliance: Memory logs can contain PII. Operators must integrate classification, retention, consent, and encryption policies before enabling memory.
- Auditability: Gateway blocks create audit trails – useful – but teams must export and retain logs per legal requirements.
- Operational cost & latency: Evaluations and policy checks add compute and runtime checks; expect some increased latency and cost that should be measured in pilots.
- False sense of safety: Prebuilt checks are helpful but not exhaustive; bespoke domain checks will likely be required for high‑risk workflows.
Competitive context
Other vendors offer pieces of this stack — function calling, tool orchestration, or policy frameworks — but AWS bundles enforcement, validation, and memory into the orchestration layer and ties it to a large set of production agents (automation, modernization, migration). For organizations already on AWS, the integration with IAM, VPC, CloudWatch, and Migration Hub reduces integration time compared with stitching third‑party toolchains.
Recommendations — who should act and what to do next
- Security & legal (0-30 days): Define natural‑language policy templates and retention policies. Map Memory use cases to data classification and consent protocols before enabling.
- Engineering (30-90 days): Run a controlled pilot using AgentCore Evaluations + Gateway on a non‑critical workflow to measure latency, cost, and false positives. Benchmark against existing test suites.
- Product & Ops (30-90 days): Prioritize use cases where audit trails and automated validations materially reduce manual approvals (e.g., automated migrations, IT ops runbooks).
- Enterprise architects (60–120 days): Update architecture diagrams and compliance artifacts to include AgentCore logs, Gateway enforcement points, and Memory storage locations for audits and eDiscovery.
Bottom line: AWS has lowered the bar for enterprise agent adoption by embedding guardrails and validation into AgentCore. That materially speeds time‑to‑value for many use cases, but it makes rigorous governance and operational testing mandatory. If you’re evaluating agent deployments this quarter, treat Policy + Evaluations as must‑test primitives, and treat Memory as a staged feature that requires legal and security sign‑off.



